New Benchmark for Android Taint Analysis
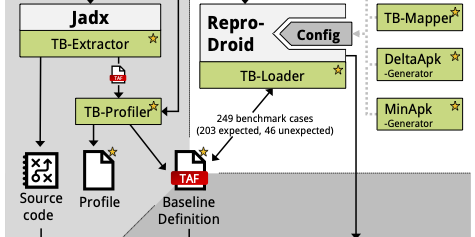
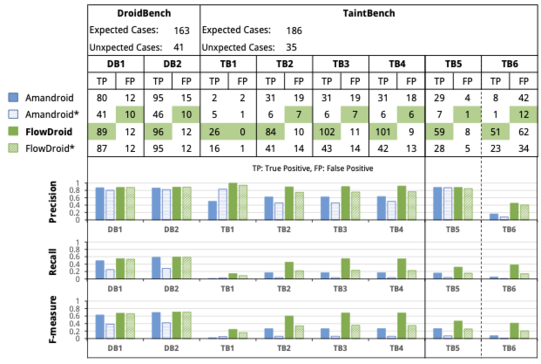
While some benchmarks based on small self-written example code for Android taint analysis such as DroidBench existed before, there was no benchmark composed out of real-world code. This impeded the reliability of the evaluations in this field as it made them restricted and hard to compare. In this new paper we provided a novel benchmark based on Android malware and a framework to created and evaluate such benchmarks. The documented taint flow baseline was established through a rigorous process. We evaluate our benchmark and methodology through several experiment involving taint analysis tools and user studies.
The Empirical Software Engineering journal is a top publication venue in the field of software systems. With an impact factor of 2.522 and an h5-index of 52 Google Scholar ranks it #6 in the field. We are happy to provide our paper open access under the German DEAL agreement.
TaintBench: Automatic Real-World Malware Benchmarking of Android Taint Analyses
Linghui Luo, Felix Pauck, Goran Piskachev, Manuel Benz, Ivan Pashchenko, Martin Mory, Eric Bodden, Ben Hermann, and Fabio Massacci
In Empirical Software Engineering, Springer Heidelberg
DOI: https://doi.org/10.1007/s10664-021-10013-5
Artifact: https://taintbench.github.io




